Here are some unnerving news for owners of ASUS routers. The Swedish publication TechWorld has revealed that USB hard drives connected to ASUS routers are easily reached through the Internet unless they are properly configured.
The following ASUS routers seem to have this "feature" available: RT-N66U, RT-N56U, RT-N15U, RT-N65U, RT-AC66U, DSL-N55U and RT-N16.
As far as I can tell these settings aren't default when you just plug an external drive in the router, however, mis-configurations are very common and are to be expected, and this really needs to be addressed. A user just clicking next-next when installing a USB drive in the router, would enable "limitless access rights".
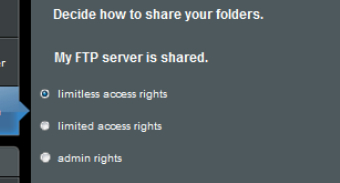
ASUS has stated in the manual and on the box that this configuration is supposed to enable completely open access to the user’s files, but checking Shodan for matches, one easily finds tens of thousands of users worldwide who have, probably unknowingly, published material such as private photo folders and pirated movies for all to see.
As usual, shady people are flocking to this, in a scavenger hunt for anything interesting. There seems to be a good deal of vacation pictures, games, school reports, CVs, music and so on. They are doing this in hope of finding some raunchy pictures, wallet.dat's or other things they can use to further intimidate/fool/hack the user.
Users do not only unknowingly share private information, they may in theory also open up to criminal charges for piracy, since there are thousands of pirated blockbuster movies available to anyone. I guess a common use-case for a NAS is to access it on your TV/HTPC/media box...
Many people are using the NAS as a backup, and now sharing their files (with write-access) to the world. I really don't understand why a setting to enable full access to the NAS drive via anonymous external FTP is even available in a home-segment router in 2014.
Another interesting thing is that some of the shared drives contain files that state things like “You were hacked because you are stupid. Password protect your router!”. People trying to be friendly(?) so the owner hopefully notices they have enabled access to the drive. This could also, but it is a long stretch, mean that the people doing this are providing some users with a kind of alibi – “I was hacked and all those movies were put there by someone else!”. This was actually quite common more than a decade ago, where FTP servers with upload access where often abused to store copyright protected material.
Problems with default configurations, and things being "too easy" to open up is nothing new, but a quick check of Shodan shows that there are close to 20.000 FTP servers worldwide with anonymous access available, presenting themselves as "ASUS".
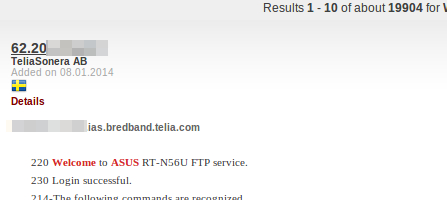
This is not an exploit or vulnerability in the ASUS router, it's more of a rather stupid combination of settings. The problematic feature of the routers in this case is the possibility to connect a drive to the router and then use it both as a NAS and as an FTP server. For many users this is just great, but it is also easy to make a possibly fatal error in the setup process, since the standard setting, according to TechWorld, is a small radio button called "limitless access rights". I really think this is a horrible setting in general, and there needs to be some big warnings if the user should choose to enable it.
ASUS’ communications marketing manager told TechWorld that they from now on will deliver the routers with a limited access default setting, since so many users miss this feature, and they intend to release an update to warn users with this setting activated. However, since that warning would only be shown to the people actually updating, and are logged in to the router interface, I suspect not many will see it...
tl;dr: Some ASUS routers make it too easy to share your USB-drive/NAS with the world.
As far as I can tell these settings aren’t default when you just plug an external drive in the router, however, mis-configurations are very common and are to be expected, and this really needs to be addressed
So by your own admission Asus is not to be blamed for the open access to people's data! This means your whole article is nothing but fearmonging. You should be ashamed of yourself!
You can't code for stupid. I guarantee that ANY product that claims to be "idiot proof" can and will be messed up by some user somewhere. So rather than blaming the tool, why not blame uneducated that tried to use the tool before they were ready? Or even better: stop blaming and start educating so as help correct and/or prevent mistakes.
But above all else, stop being a smacktard.
Hi, and thanks for your lovely comment!
I totally agree that people need to be educated and more concerned regarding what they do, and that they really shouldn't just click next-next, or try to figure out whichever button gives them the least amount of questions.
Looking at the Shodan data, about 37% (19933/53466) of the ASUS FTP matches are allowing anonymous FTP to the world. If 37% of the users fail to configure it correctly, there are definitely improvements to be made, and ASUS really should have some UI/UX people look at it.
Nothing can be idiot-proof, but there is no reason to make the defaults, when you add a drive to share, insecure.
As I clearly stated in the original article (www.pcworld.no/article281004.ece) this is not a technical issue by itself. It's a result of a bad user Interface. The numbers of open routers are so high that it is a problem.
We can always "blame stupid users". A manufacture of a consumer product should always assume that the user is stupid in my opinion. Make it safe as default when the feature is enabled. If the user really wants it open, he can do that - not the other way around.
That said, there is also quite many open Netgear-products out there - both WRT-series of routers and ReadyNAS-series of NAS-units. The problem for Asus here is also their high sales figures.
Clas